Last updated on April 15th, 2024
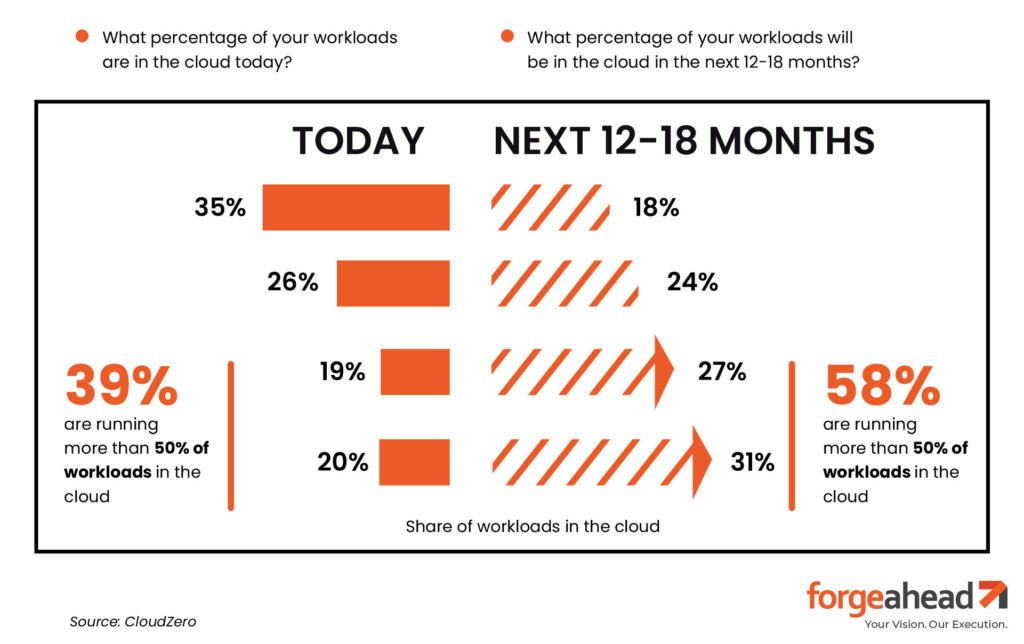
94% of enterprises already utilize cloud services.
This statistic underscores the shift towards cloud computing, elevating the importance of cloud infrastructure security best practices in today’s digital ecosystem.
As the reliance on cloud platforms grows, so does the spectrum of cyber threats, from data breaches to unauthorized access, presenting a myriad of challenges for businesses aiming to protect their digital assets.
Coupled with the stringent compliance mandates across industries, ensuring robust cloud security becomes a complex but essential task.
This blog will help you get into the critical need for stringent cloud infrastructure security measures, guiding you through the challenges and offering strategies to enhance your organization’s defense against the evolving cyber threat landscape
Safeguarding the Cloud: The Keystone of Digital Defense
Let’s break down why robust defenses in the cloud are non-negotiable and explore the myriad benefits they bring to the table.
Why Is Cloud Infrastructure Security Important?
Cloud infrastructure security forms the backbone of safeguarding your digital assets against the onslaught of cyber threats.
From sophisticated phishing attacks to complex data breaches, the security measures you employ act as the gatekeepers of your organization’s data integrity and confidentiality.
Moreover, as regulatory landscapes evolve, maintaining compliance with standards like GDPR, HIPAA, or PCI DSS becomes a critical aspect of your cloud strategy, ensuring you’re not just secure but also within the bounds of legal requirements.
Benefits of Cloud Infrastructure Security
Business Continuity:
Ensures operations remain uninterrupted, even in the face of cyber threats, safeguarding against costly downtimes.
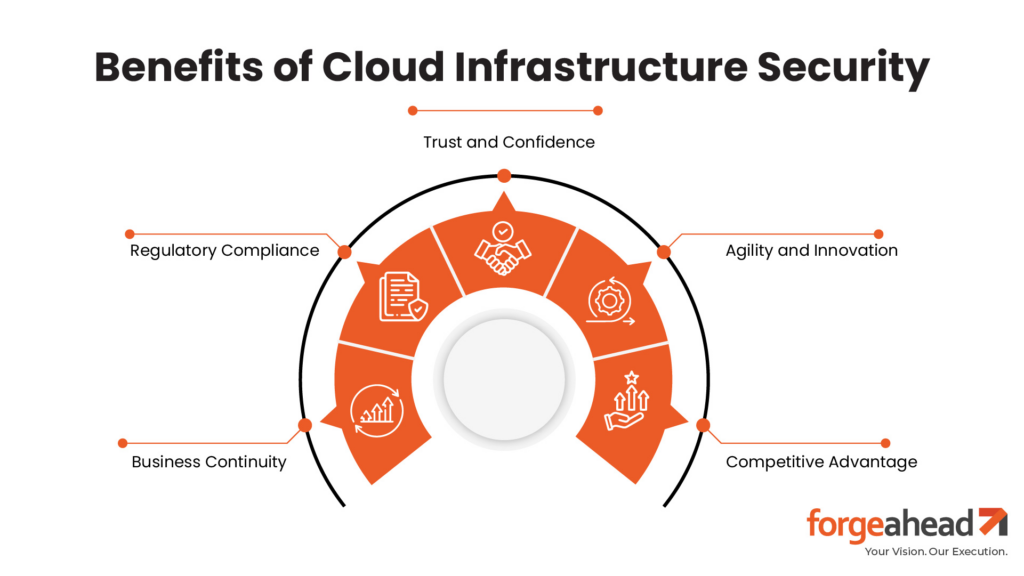
Trust and Confidence:
Builds a strong foundation of trust with customers and stakeholders by demonstrating a commitment to protecting sensitive data.
Regulatory Compliance:
Facilitates adherence to evolving regulatory standards and compliance mandates, avoiding legal penalties and reputational damage.
Agility and Innovation:
Empowers organizations to embrace digital transformation with confidence, enabling quicker adoption of new technologies without the burden of security concerns.
Competitive Advantage:
Positions your business as a secure, reliable partner in an ecosystem where data security is a critical decision factor for clients and partners.
Strengthening Access Controls in Cloud Infrastructure
Implementing strong access controls is a cornerstone among cloud infrastructure security best practices, crucial for safeguarding your cloud environment. It ensures that only authorized users can access sensitive information, acting as the first line of defense against unauthorized entry.
Here’s how you can tighten security with effective access management strategies:
Multi-Factor Authentication (MFA)
MFA adds an extra verification step to the login process, requiring users to provide two or more pieces of evidence to access their accounts. This could be something they know (password), something they have (a phone), or something they are (fingerprint). By adding this layer, you significantly lower the risk of unauthorized access.
Role-Based Access Controls (RBAC)
RBAC limits access to information based on the user’s role within your organization. It ensures that employees only have access to the resources necessary for their job functions. This method streamlines operations while enhancing security by minimizing each user’s potential attack surface.
Locking Down Data: Encryption and Privacy in the Cloud
In the digital age, data encryption isn’t just a best practice—it’s a necessity for safeguarding your sensitive information.
Whether your data is on the move or at rest, encryption acts as a secure vault, ensuring that your information remains confidential and tamper-proof.
Utilizing data encryption in cloud environments is a fundamental aspect of protecting privacy and ensuring data integrity.
Encryption in Transit
Imagine your data as a valuable asset being transported in an armored truck. Encryption in transit protects your data as it travels across the internet, shielding it from prying eyes and ensuring that it arrives at its destination securely.
Encryption at Rest
When your data is not being actively moved, it’s stored—or “at rest.” Encryption at rest is like having a state-of-the-art security system for your digital vault, making your data unreadable to unauthorized users, even if they manage to bypass other security measures.
Implementing robust encryption and privacy measures is crucial for maintaining the integrity and confidentiality of your data.
By ensuring your information is encrypted both in transit and at rest, you create a formidable barrier against cyber threats, safeguarding your organization’s privacy and security in the cloud.
Vigilance in the Cloud: Monitoring and Incident Response
In the sprawling landscape of cloud computing, continuous monitoring and a swift incident response plan are your watchtowers and cavalry.
Adopting rigorous cloud security monitoring practices ensures you’re always one step ahead, ready to act at the first sign of trouble.
Continuous Monitoring:
It’s about keeping a constant eye on your digital environment. This unblinking vigilance helps detect unusual activity that could signal a breach, allowing you to act before it escalates.
Comprehensive Incident Response:
When a breach occurs, time is of the essence. A well-crafted incident response plan is your blueprint for action, detailing steps to contain, assess, and remediate threats, minimizing their impact.
Embracing these measures fortifies your defenses, ensuring you’re prepared to tackle security breaches head-on, maintaining the trust and confidence of your stakeholders.
Navigating the Compliance Maze in Cloud Environments
Navigating cloud compliance management in the cloud isn’t just a checkbox—it’s a commitment to safeguarding your data in line with global standards.
Understanding and adhering to regulations like GDPR, HIPAA, and PCI DSS can seem daunting, but it’s essential for operating confidently in the digital space.
Understanding Compliance Requirements:
Start by getting to grips with the specifics of each regulation relevant to your industry and region. This knowledge base is crucial for developing strategies that align with legal expectations.
Implementing Compliance Measures:
With a clear understanding of your obligations, you can tailor your cloud infrastructure and policies to meet these standards. Regular audits and updates ensure your compliance posture evolves alongside regulatory changes.
Mastering compliance management in cloud environments not only protects you from legal penalties but also reinforces your commitment to data protection, enhancing your reputation in the market.
Cloud Infrastructure Security Best Practices
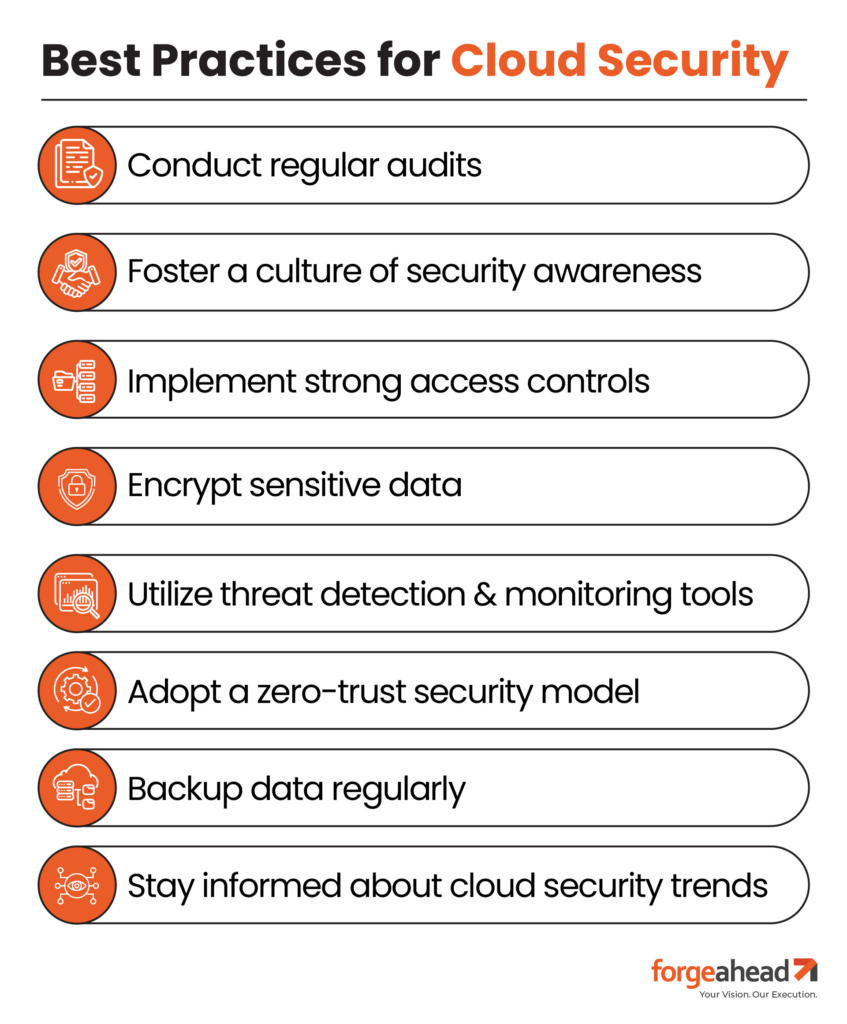
Securing your cloud infrastructure through cloud infrastructure security best practices is a continuous process that demands vigilance and strategic planning.
Here are some key practices to keep your digital assets safe:
Conduct Regular Security Audits:
Routine inspections of your cloud infrastructure can reveal vulnerabilities, allowing you to fortify your defenses before attackers can exploit them.
Foster a Culture of Security Awareness:
Educate every team member on the importance of security. Regular training and updates can transform your staff into the first line of defense against cyber threats.
Implement Strong Access Controls:
Ensure that access to cloud resources is tightly controlled with strong authentication methods. Utilize role-based access controls (RBAC) to grant permissions appropriate to each user’s job function, minimizing the risk of internal threats.
Encrypt Sensitive Data:
Protect your data—both in transit and at rest—by implementing robust encryption methods. This ensures that even if data is intercepted or accessed, it remains unreadable to unauthorized users.
Utilize Threat Detection and Monitoring Tools:
Deploy advanced security solutions that monitor your cloud environment in real-time, detecting and alerting you to potential threats before they escalate.
Adopt a Zero-Trust Security Model:
Operate on the principle that no one, inside or outside the network, is trusted by default. Verify every access request as if it originates from an open network, regardless of where the request originates or what resource it accesses.
Backup Data Regularly:
Regular backups protect against data loss due to security breaches, system failures, or disasters. Ensure your backup strategy includes secure storage locations and regular testing of backup restores.
Stay Informed About Cloud Security Trends:
The cybersecurity landscape is ever-evolving. Stay updated with the latest security threats and advancements in cloud security technologies to continuously refine your security strategies.
By integrating these additional practices, you not only enhance your cloud infrastructure’s security but also build a resilient environment capable of withstanding and adapting to the complexities of modern cyber threats.
The Future of Cloud Computing
As we peer into the horizon of cloud computing, the trajectory is clear: security will continue to be the linchpin that determines its success and sustainability.
The future of cloud computing promises innovative technologies like edge computing, quantum computing, and AI-driven security measures, each bringing its own set of challenges and opportunities for security practices.
Exploring The Future of Cloud Computing reveals how cloud infrastructure providers continue to evolve, offering more robust security solutions.
Cloud Security Champions: Dropbox and Netflix

Dropbox and Netflix exemplify how cloud infrastructure services companies shine brightly as beacons of cloud security excellence.
Dropbox
Dropbox, a titan in cloud storage and file sharing, has transformed data security into an art form. At the heart of its strategy lies a trifecta of secure networks, robust encryption, and multi-factor authentication (MFA).
This layered approach ensures that user data, from precious family photos to critical business documents, remains under lock and key. By encrypting data both in transit and at rest, Dropbox creates a veritable digital vault.
Adding MFA into the mix is like having an ever-vigilant guardian, providing an additional layer of security that keeps unauthorized access at bay.
Netflix
Netflix, the colossus of streaming, showcases its mastery of cloud security by deploying an advanced cloud security platform.
This platform is the digital equivalent of a medieval castle, equipped with high walls (firewalls), concealed passages (encryption), and vigilant guards (security tools).
These measures ensure that subscribers can binge-watch their favorite shows without a hint of worry, as their data is guarded against cyber threats.
Netflix’s commitment to cloud security enables seamless, secure access to entertainment for millions of users worldwide, setting the gold standard for protecting user data in the cloud.
Securing the Cloud: A Blueprint for Digital Fortitude
In the ever-evolving landscape of digital technology, the security of cloud infrastructure emerges as a paramount concern.
This guide has traversed the pivotal strategies and best practices essential for fortifying your cloud environment against the myriad of cyber threats lurking in the digital shadows.
Embracing these methodologies is not just a recommendation; it’s a necessity for safeguarding the digital assets that form the backbone of your business. Let the insights shared here inspire you to enhance your cloud security measures, ensuring your organization stands resilient in the face of cybersecurity challenges.
Embrace this blueprint for digital fortitude, and lead your cloud infrastructure into a future where security and efficiency coalesce.
FAQs
What are the top cloud computing security challenges?
Top challenges include data breaches, unauthorized access, compliance with regulatory standards, securing data in transit and at rest, and managing the shared security responsibility model.
What are the best practices for securing cloud infrastructure?
Best practices involve implementing strong access controls, encrypting data in transit and at rest, conducting regular security audits, and maintaining continuous monitoring for threats.
What are the three pillars of cloud security?
The three pillars are confidentiality, ensuring data is accessed only by authorized users; integrity, protecting data from unauthorized changes; and availability, ensuring data is accessible when needed.
How can organizations prevent data breaches in the cloud?
Preventing breaches requires encryption of sensitive data, using robust authentication methods, and regularly updating and patching cloud services and applications.
Why is continuous monitoring vital for cloud security?
Continuous monitoring detects real-time threats and unusual activities, allowing for immediate response to secure the cloud environment.



